
Most of my posts focus almost exclusively on retirement stewardship and planning issues but with a holistic approach (time, talents, treasure, and testimony).
I have also written a two-part series about the stewardship of paper and digital assets. Part one addressed device, password, and file management, and how to keep all these things safe and secure. Part two talked about preventing and dealing with identity theft.
I’m now a few years into retirement and heading into my seventies, and I expect to encounter practical issues that I hadn’t anticipated and may not have written about.
As we all know, ”stuff happens.” (That’s not in the Bible exactly, but here’s my paraphrase of Ecc. 8:7: ”We don’t know what will happen, and no one can tell us what will happen, but we know things will happen.”)
Fortunately, a little planning and groundwork before something comes up can save a lot of time, effort, and trouble on the back end (Prov. 22:3).
For example, due to a situation of a friend of mine, I realized that I hadn’t set up any backup options for my Two-Factor Authentication (2FA)-protected accounts to prepare for a lost, broken, unavailable, or new phone. So, I looked into the options and want to share what I learned.
Two-factor authentication (2FA)
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to an application, online account, or network. Rather than just requiring a username and password, MFA requires one or more verification factors, decreasing the probability of unauthorized access to your account or data.
Two-factor authentication (2FA) is a type of multi-factor authentication and a widely used and effective mechanism. Hopefully, you already have it enabled on accounts such as Apple, Google, Microsoft, Facebook, Dropbox, etc. You may also use it for your banking, brokerage, and credit card accounts. If so, you probably know what it is and how it works, so you can skip to the next section (you’re welcome).
Put simply, 2FA gives you additional security for logins to apps, websites, and devices just using your ID and password. The ”two factors” generally refers to something you know (like your user ID and password or passcode) and something you own (such as a smart card or USB key, but for most people, it’s their smartphone).
Generally, 2FA works as follows: You first have to enable it, which is usually done in the security settings for your account profile on the website or app you are using. You’ll be asked how you want to receive the 2FA authorization code.
Most people use one of three mechanisms to use 2FA on their devices: 1) text message, 2) email, 3) phone call, or 4) third-party software (such as Authy or an Apple, Google, or Microsoft authenticator app—more on that later). Text messages are the most common.
If any of your accounts use 2FA by sending an email, consider setting up an email account with a random name solely to receive 2FA passcodes. Set up a notification in that email account to alert you anytime you receive an email.
Then, when you sign in with your user ID and password, you’ll be asked to enter a code that will be sent in the way you specified—text, email, voice call, or your 2FA app. You enter the code to complete the authentication process. Easy peasy!
That second layer of security is what makes 2FA effective. But, as you can see, it has one big drawback: what if you lose or can’t access your smartphone for some reason to retrieve the authorization code.
Your 2FA device is lost, stolen, or broken
There are two different scenarios where 2FA and a lost, stolen, unavailable, or out-of-service device can come into play:
Scenario One: You’re the primary account owner (or co-owner) with a user ID and password and using 2FA, and your device that receives the 2FA codes has been lost, stolen, or isn’t working.
Scenario Two: You’re acting in place of or on behalf of the account owner and may or may not have a user ID and password and don’t have the device that receives the 2FA codes.
The first scenario is the most common. But for some (like my wife and I), a lost, stolen, or broken device (such as my iPhone) would be less of a problem because I can still get the 2FA code via my iPad or Mac. However, if I only had one device set up to get the code (such as my iPhone) and couldn’t access it, that would present a problem.
In the second scenario—someone acting on behalf of a deceased, incapacitated, or otherwise unable or unavailable spouse or relative—the problem is more complicated.
If the account owner is deceased and no security information has been left behind, you’ll have to follow “next of kin” procedures for each account (and each will be a little different). In most cases, proof of death and financial power of attorney will be sufficient, depending on the deceased’s will or trust estate provisions.
Financial power of attorney may be sufficient in cases of incapacitation or other types of unavailability. Without that, and in some states, legal authorization from a court with appropriate jurisdiction will be required.
What to do
In scenario one, the problem is the inability to retrieve the 2FA code. Without it, you can’t log into the app or website to change your security settings to a different device or delivery method (such as email).
But that’s the point—the whole purpose of 2FA is to prevent access to your accounts if the person wanting access doesn’t have access to your phone (or whatever authenticating device you’ve chosen). Therefore, if you’re that person, you don’t have many options to work around this requirement when you lose that device.
Some people panic when they lose their phone and immediately assume they need to “wipe” it. When you attempt it (via your computer), you suddenly realize that a 2FA code has been sent to the phone you are trying to wipe—the one you no longer have. Yikes!
Reality sets in—you can’t input the code because you can’t receive it; therefore, you can’t wipe the device. Now you’re freaked out because you know your phone is out there with all your info on it (albeit an encrypted phone with a locked screen). You can’t use the device for 2FA when you try to access other apps and websites.
You can try to contact the company that supports the app or runs the website you’re trying to access. But an account access approval process could take several days, assuming the company will work with you on it (most will if you can supply lots of other security information).
If you can’t locate it or unlock and erase it remotely, you’ll have to call your carrier to get the phone shut down (i.e., made unusable), even with a new carrier or SIM card. Then you can get a new device and activate it with the same phone number, which will enable you to receive messages.
Scenario two is similar but a situation where a second party may or may not have access to the account owner’s device that is used to receive the 2FA codes.
If they have the device, they will need access to the screen lock codes to use them. Without the code to unlock them, the assisting person is stuck. (This is why I strongly suggest that everyone have this information written down somewhere safe.)
In that case, they’ll need legal authorization to do so, and even then, the smartphone manufacturer (such as Apple, Samsung, or Google) may make it very difficult (and with good reason—they are obliged to protect their customer’s data, and you are not that person).
If the second party has the user id and password for an account but doesn’t have the device used to receive the 2FA code, then they are in much the same position as the owner in scenario one, who has lost their device. Their options are limited.
The goal, therefore, is to devise ways to prevent the 2FA code problem from occurring in the first place (beyond not losing the device). If the device isn’t lost, but it (or its owner) is temporarily unavailable, then it may be just a waiting game. Otherwise, legal action may be required to access the app or website. Neither are desirable options.
Back-up plan for two-factor authentication
The best solution to both of the above scenarios is to have a backup option for 2FA. There are a couple of good ones.
The first option is the simplest and most common. It’s so easy that it is often overlooked. All you need to do is to add a second device telephone number or email that you can request the authorization code to be sent to if the main one isn’t working.
For example, in my Fidelity account, after I log in, I can go to Profile=>Security Center=>Extra Login Security (2-Factor Authentication at Login). If I click on the ”Enable” button, I’ll see this series of screens:
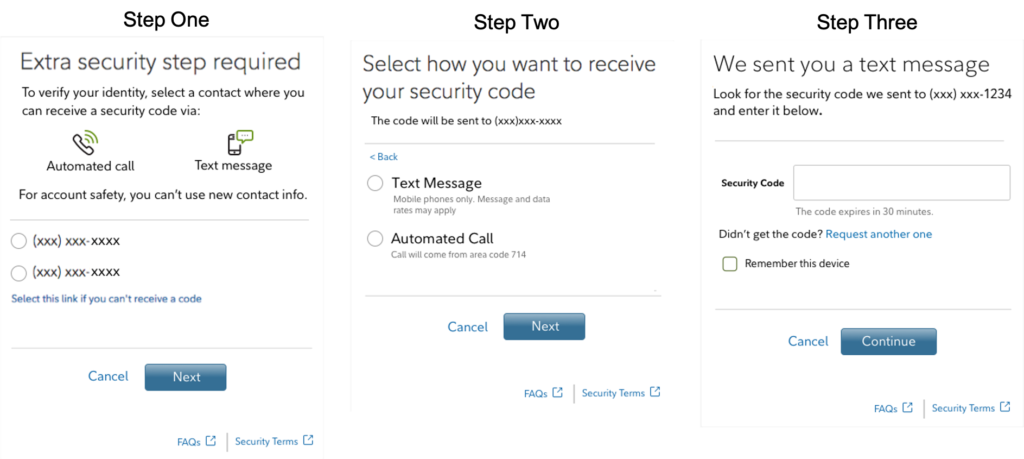
Other financial sites will operate very similarly to Fidelity’s.
Note that in step one there is an option to set up more than one telephone number. In my case, I added my wife’s mobile number to my profile. If my phone is lost, stolen, or otherwise unavailable, I can request that the 2FA code be sent to her phone instead. Done!
Step Four

I must confess: I only recently went in and added her phone number to my profile, so I know how easy it is to overlook that step. If you don’t have a spouse, use another number for someone you trust whose phone you can have quick and easy access to.
The second option, which most security experts consider more effective in thwarting hackers, is a little more ‘techie,’ so it takes more time to understand and implement. Should you look into it and decide that it’s too complex, keep at it—it can be a big step up in security.
This option is to use an authenticator app installed on all your devices (smartphone, tablet, laptop, etc.). That would be a step up security-wise because a key weakness of using SMS messages to receive 2FA codes is that hackers can reroute text messages to get the codes meant for you.
When you use an authenticator app, the codes it generates don’t ever get routed over your mobile network (text or email), which lessens the chance of your security being compromised. Plus, the codes change every minute or so and can only be read in the app on your phone.
I’ve been looking into this. I’m considering several options: Apple, Authy, and the LastPass authenticator—Apple because its free, Authy (a 3rd party app) because it is highly rated, and LastPass because I already use it as my password vault. (My preference is to use LastPass.)
However, I learned that Fidelity (where I have my financial accounts) only supports one authenticator app: Symantec’s free Validation and ID Protection (VIP) Access app. So I am still looking at my options since I’d prefer to use just one app for all my 2FA accounts.
You may be wondering how an authenticator app helps with the lost or stolen smartphone problem. Well, it does so in a couple of ways:
First, you can install the app on more than one device; so if one’s unavailable, another may be (similar to SMS).
Second (and this is a significant improvement over a backup telephone number), you can save backup account codes provided by the sites using the authenticator app somewhere safe but accessible, such as in an encrypted file or a password manager like LastPass on your computer.
Your authenticator app codes change dynamically, but these backup codes donate change. However, once you use one, you can’t use it again.
If you lose your phone, those codes will work in place of the dynamic codes generated by the authenticator app, allowing you to still log in to the site if your phone is lost, stolen, or broken.
They will also help you if you are locked out of an account for any reason or if you forget to disable the authenticator app before giving it away or selling it (or can’t because your phone has been lost or stolen). You can use the backup codes to get access to your account. You can also reinstall the authenticator app or your new phone, generate new codes, and get back to business-as-usual.
If you change phones and you’re using SMS, changing phones but keeping the same number, you’ll simply activate your new phone and get the 2FA codes just as before. If you use an authenticator app (like Authy), you should be able to swap the app and all its settings when you set up your new phone from a backup.
Next steps
If you haven’t set up 2FA on your accounts, I encourage you to do it now. If you have, make sure you have a backup in place—it’s wise stewardship of your digital assets (Prov. 22:3). Plus, it will be a huge help if you lose your device, or if someone is acting in your stead without it, or if they do have it but are unable to access it.
